Defining the authorization scheme
5 Tasks
1 hr 30 mins
Scenario
MDC wants to implement the following security requirements in its organization:
- City Managers and Accountants can see only financial information that belongs to their city.
- Executive Managers can see financial information that belongs to all the cities.
- Business partners can only see the delivery requests they submit.
The following table provides the credentials you need to complete the challenge:
| Role | User name | Password |
|---|---|---|
| Administrator | Admin@deliveryservice | rules |
The following table provides a list of sample users that are available for testing:
| Department | Role | User name | Password |
|---|---|---|---|
| Executives | Executive Manager | ExecutiveManager@MDC | rules |
| City Manager | City Manager for Boston | BostonCityManager@MDC | rules |
| City Manager | City Manager for Springfield | SpringfieldCityManager@MDC | rules |
| City Manager | City Manager for Worcester | WorcesterCityManager@MDC | rules |
| Account | Account for Boston | BostonAccountant@MDC | rules |
| Account | Account for Springfield | SpringfieldAccountant@MDC | rules |
| Account | Account for Worcester | WorcesterAccountant@MDC | rules |
Design and implement the authorization scheme to fulfill the requirements.
- Identify access groups and roles.
- Implement the above requirements.
Detailed Tasks
1 Review the solution detail
Review the following tasks for the solution:
Assign Access Groups and roles
This task involves assigning Access Groups and roles for an application.
System-generated roles
The New Application wizard creates a DeliveryService:Administrator / DeliveryService:Authors role and two user roles: DeliveryService:User and DeliveryService:Manager.
Users with the DeliveryService:User role can open any Case in the application and perform any Assignment. In the user-specific role, you can provide the ability to create and update reports, delegated Rules, and Work Groups.
Create delivery service Personas
When you create Personas associated with the Delivery service, the system automatically creates corresponding Access Groups and Access Roles.
Create the following Personas; permissions and privileges are granted based on the Personas. Save the roles to the DeliveryService Ruleset.
| Persona | Label | Access Group | Dependent on |
|---|---|---|---|
| Executive Manager | Executive Manager |
DeliveryService:ExecutiveManager |
DeliveryService:User4 |
| Business Partner | Business Partner | DeliveryService:BusinessPartner | DeliveryService:User4 |
| Accountant | Accountant | DeliveryService:Accountant | DeliveryService:User4 |
| City Manager | City Manager | DeliveryService:CityManager | DeliveryService:User4 |
| External User | External User | DeliveryService:ExternalUser | DeliveryService:Guest |
- DeliveryService:User4 is dependent on MDC:User4
- MDC:User4 is dependent on PegaRULES:User4
- DeliveryService:Guest is dependent on MDC:Guest
- MDC:Guest is dependent on PegaRules:Guest
Create MDC Delivery Service Work Groups
Create the following Workgroups for each department because work is often assigned to them. Save the Work Groups to the DeliveryService Ruleset.
| Workgroup identifier | Description | Manager | Default Workbasket |
|---|---|---|---|
| Accountant | Accountant | ExecutiveManager@MDC | AccountantWQ |
| Business Partner | Business Partner | ExecutiveManager@MDC | BusinessPartnerWQ |
| CityManager | City Manager | ExecutiveManager@MDC | CityManagerWQ |
Update the Personas with the corresponding Work Groups.
2 Enable attribute-based access control security
Use attribute-based access control (ABAC) to configure your authorization scheme.
Restrict access to financial information by using ABAC
To restrict access to the financial information as described in the scenario, perform the following actions:
- Create IsAccountant and IsCityManager Access When records to test if a user belongs to the Accountant or CityManager Access Group.
- Create a CityManagerAndAccountant access control policy condition that references your new Access When records.
- Create a RestrictFinancialInformation read properties access control policy that references your new access control policy condition. Users defined in the RestrictFinancialInformation access control policy condition can view the invoice data records.
Create City Manager and Accountant Access When records
- In the Records Explorer, expand the Security category.
- Select the Access When record type.
- Click Create.
- On the new record form, enter the following information:
- In the Label field, enter IsCityManager.
- In the Apply to list, enter MDC.
- In the Add to ruleset field, enter DeliveryServiceAuthorization.
- Click Create and open to create the new Access When record.
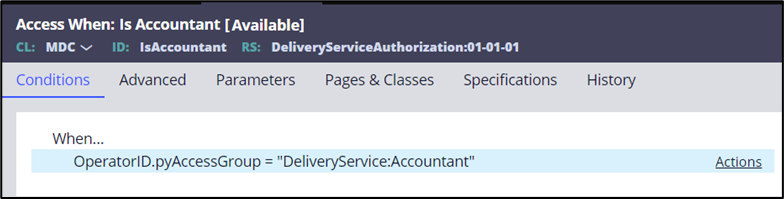
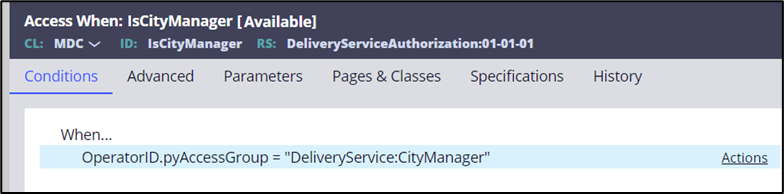
- On the Conditions tab, enter the following When expression:
pxThread.pxCurrentAccessGroup = "DeliveryService:CityManager".
The following figure shows the completed Conditions tab:
- Save the new IsCityManager access When record.
- Repeat steps 1-3.
- On the new record form, enter the following information:
- In the Label field, enter IsAccountant.
- In the Apply to list, enter MDC.
- In the Add to ruleset field, enter DeliveryServiceAuthorization.
- Click Create and open to create the new access when record.
- On the Conditions tab, enter the following When expression:
pxThread.pxCurrentAccessGroup = "DeliveryService:Accountant"
The following figure shows the completed Conditions tab:
- Save the new IsAccountant Access When record.
Create an CityManagerAndAccountant access control policy condition
- Open the Records Explorer.
- Expand the Security category.
- Select Access Control Policy Condition record types.
- Click Create.
- On the new record form, enter the following information:
- In the Label field, enter CityManagerAndAccountant.
- In the Apply to list, enter MDC-Data-Invoice.
- In the Add to ruleset field, enter DeliveryServiceAuthorization.
- Click Create and open to create the new CityManagerAndAccountant access control policy condition.
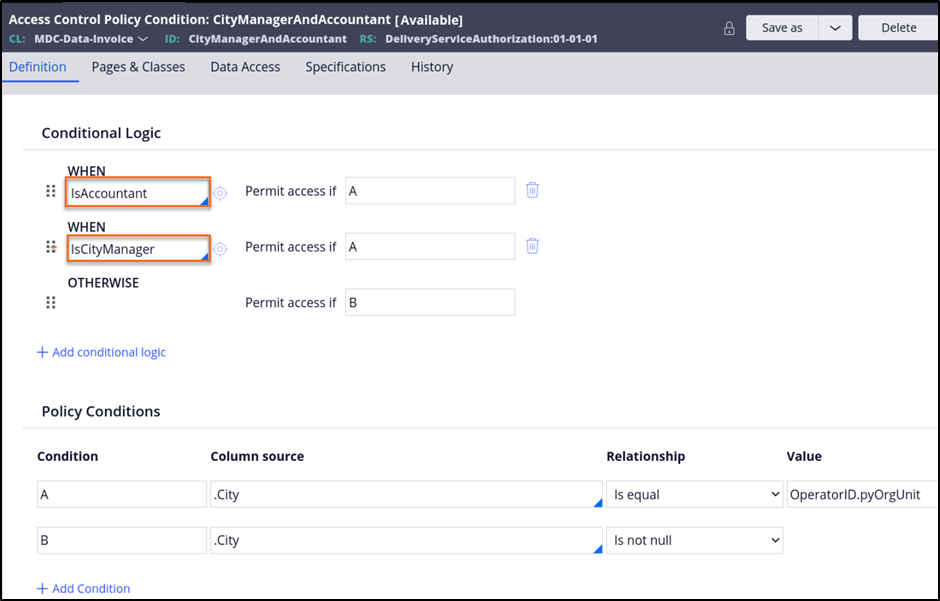
- On the Definition tab of the access control policy condition, in the Conditional Logic section, add the IsCityManager and IsAccountant Access When records that you created.
- Optional: In the Policy Conditions section, specify a condition that always returns false to ensure that access is only provided if one of the Access When Rules evaluates to true.
- Save the new CityManagerAndAccountant access control policy condition record.
The following figure shows the completed Definition tab:
Create a RestrictFinancialInformation access control policy
- Open the Records Explorer.
- Expand the Security category.
- Select Access Control Policy record types.
- Click Create.
- On the new record form, enter the following information:
- In the Label field, enter RestrictFinancialInformation.
- In the Action field, enter PropertyRead.
- In the Apply to list, enter MDC-Data-Invoice.
- In the Add to ruleset field, enter DeliveryServiceAuthorization.
- Click Create and open to create the new RestrictFinancialInformation access control policy.
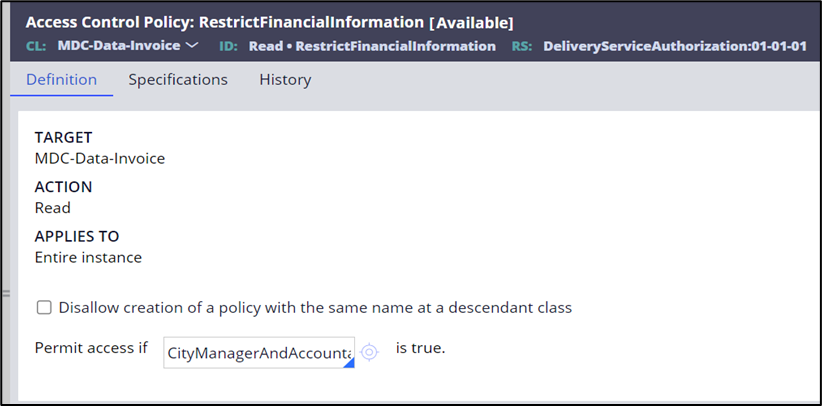
- On the Definition tab of the access control policy, in the Permit access if field, enter the CityManagerAndAccountant policy control condition that you created.
The following figure shows the completed Definition tab:
- Save the new RestrictFinancialInformation access control policy.
3 Restrict access to Cases by using ABAC
Each persona must have access to intended Cases and data objects only.
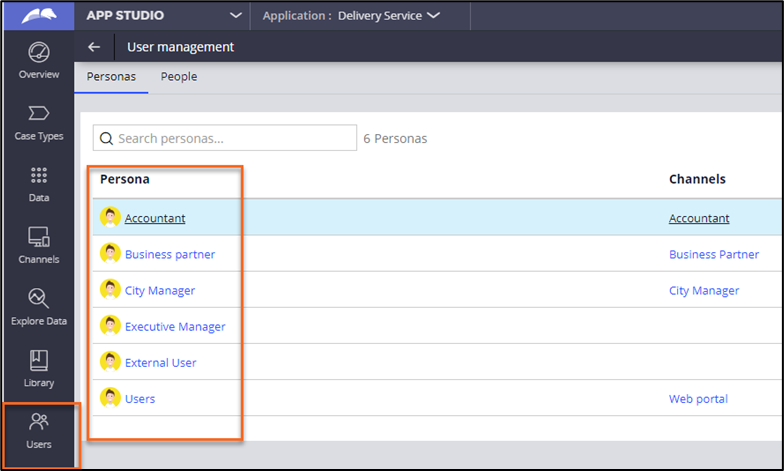
- In the navigation pane of App Studio, click Users, as shown in the following figure:
- On the Personas tab, select the required Persona from the list, as shown in the following figure:
- Change the roles for selected persona.
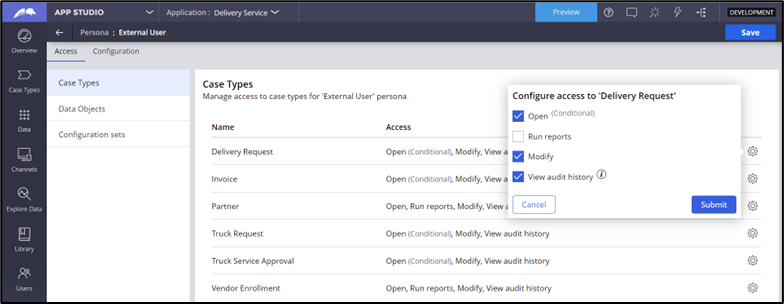
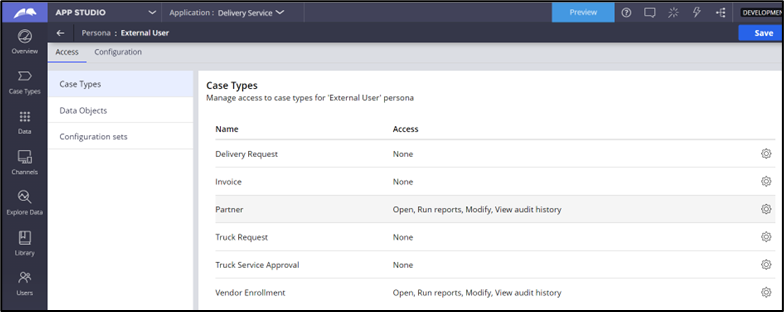
- Update the Cases for which external user access is required, and then ensure that you remove access to other Cases, as shown in the following figure:
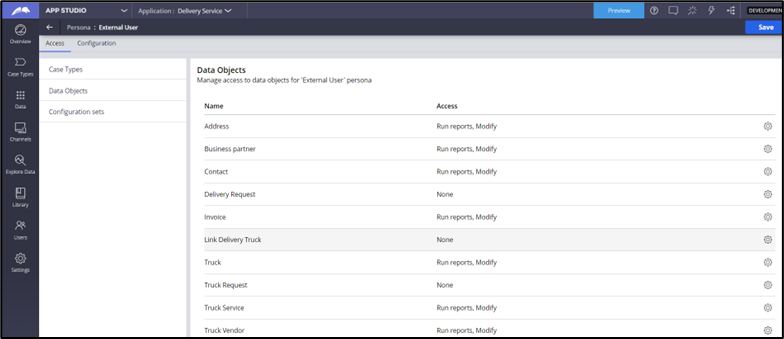
- Update the data objects for which access is required.
- Update the security of the other Personas in App Studio.
4 Confirm your work
- Log in as a registered business partner, and then create a Delivery request.
- Wait for the job scheduler to assign a truck or manually run the utility of the job scheduler for test purposes.
- As a city manager of the corresponding city for which the delivery request is submitted, complete the Pickup and Delivery Steps of the Truck request to generate an Invoice Case.
Truck requests for other cities must not be visible or accessible through search. - Log in as an accountant, and then provide the required approval for the Invoice of Delivery and Truck requests.
- As a business partner, complete the payment on the Delivery request.
- As a city manager, complete the feedback on the truck.
Throughout the process, the City Manager and Accountant should not have access to the Cases and data related to other cities.
5 Review the solution
The solution RAP file provided in the Application Design mission of this mission does not contain a complete implementation of all the authorization requirements specified in the Front Stage Scenario Requirements. You can implement all the given requirements by using a combination of RBAC and ABAC.
To review the implemented solution, switch the application to Delivery Service Authorization when you log in as Admin@DeliveryService.
Confirm your work
Available in the following mission:
If you are having problems with your training, please review the Pega Academy Support FAQs.
Want to help us improve this content?